DARWIS Threat Intel API
DARWIS Threat Intel API
can be used on multiple applications like KYC, Loan applications in BFSI
comes as WS3, WS4, WS4.AR, WS6
Darwis.WS3
Powerful security solution for API-based applications
Darwis.WS4
is primarily used in deception technology/Honeypot, where the hashes are checked initially with reputation API.
A malware analysis API is used to check if an uploaded file is malware or not. This uses different technologies to determine if a file is malware.
Darwis.WS4.AR
is written mainly for BFSI and third-party aggregators in India. This is finetuned for KYC documents where the majority of files are clean or unique files (where WS4 and WS3 may not give optimal results).
This can be used by customers when processing user data (KYC documents) in applications like loan management, lead management, and KYC applications
Darwis.WS6
is written mainly for email/IP/Inbox validation. Helps deanonymize emails/IP/inbox.
It can be built into any application having a login/registration page, data collection forms in any application help mitigate the risk of the backend support team desktop getting infected by APT actors.
The APT group has successfully exploited this mechanism to enter the internal network.
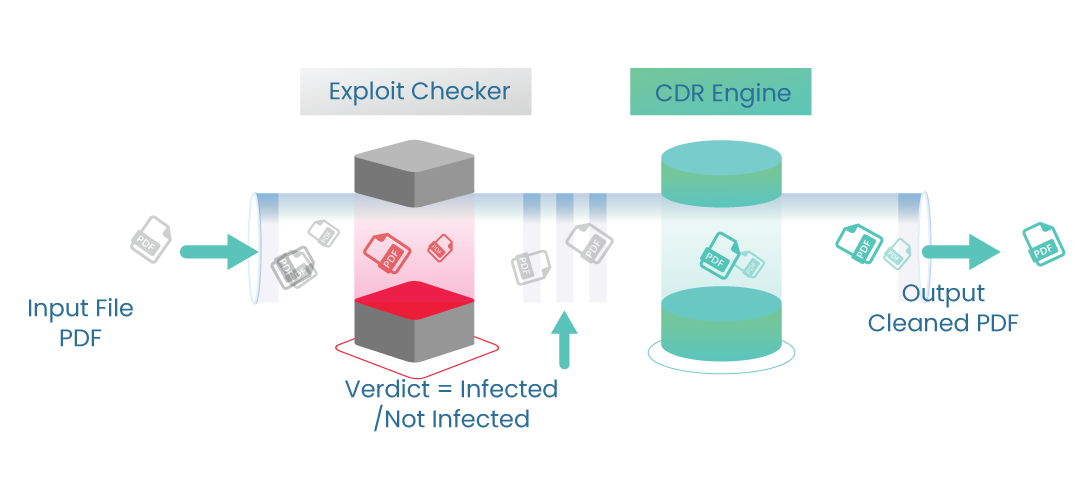
Darwis CDR API - WS7
“WS7 is written using the CDR (Content Disarm and Reconstruction) method also known as Threat Extraction”
It Proactively protects against known and unknown threats contained in documents/image/pdf by removing malware, exploits.
This enables CDR to offer true zero-day prevention, while delivering files to users/customers quickly.
WS7Docs is primarily for pdf file. In the process of checking for malicious files/exploits, the pdf document is disarmed and reconstructed.
WS7IMG is primarily for image files with image extensions such as TIFF, JPG, PNG, GIF, BMP etc. A unique technology is used to disable the malicious stegano malware which could be hidden inside the image. The disarmed image is optionally given as a JPG file.